Hunt:
Who runs netsh + context?
How often Set-MpPreference is used?
Who creates exclusions, and when?
Hunt:
Who runs netsh + context?
How often Set-MpPreference is used?
Who creates exclusions, and when?
AMSI bypass (reflection, AMSIReaper, NukeAMSI)
COM hijacking for persistence
Defender exclusions (paths/exts/procs)
UAC bypass (EnableLUA)
Firewall off (netsh)
Set-MpPreference abuse
C2: Blogspot → bitbucket redirects
AMSI bypass (reflection, AMSIReaper, NukeAMSI)
COM hijacking for persistence
Defender exclusions (paths/exts/procs)
UAC bypass (EnableLUA)
Firewall off (netsh)
Set-MpPreference abuse
C2: Blogspot → bitbucket redirects
Distribution Locations:https://t[.]me/+seHLUhOHbVhMDM0, breachforums, cracking[.]org,hard-tm[.]su, nohide[.]space, darknetarmy[.]com, niflheim[.]world,nulledbb[.]com, niflheim[.]world.
Distribution Locations:https://t[.]me/+seHLUhOHbVhMDM0, breachforums, cracking[.]org,hard-tm[.]su, nohide[.]space, darknetarmy[.]com, niflheim[.]world,nulledbb[.]com, niflheim[.]world.
Telegram distribution via t[.]me/hitbase, t[.]me/sharmamod disguised as IPTV or Netflix access.

Telegram distribution via t[.]me/hitbase, t[.]me/sharmamod disguised as IPTV or Netflix access.
37.27.63.3
45.89.196.115 (reported in the past)
Will blog on more details.
37.27.63.3
45.89.196.115 (reported in the past)
Will blog on more details.
Adversary Infra:
37.27.63.3:443 (kyfjlijv[.]ru) -
84.200.154.182 (not detected by VT yet)
smkuksool[.]com
2a01:4f9:3081:3098:0:0:0:2
services.ssh.server_host_key.fingerprint_sha256: 92709a98601c28a87fa307e63ae8bc60f870c6b9533a2d50bdb2c16fda205c37
Adversary Infra:
37.27.63.3:443 (kyfjlijv[.]ru) -
84.200.154.182 (not detected by VT yet)
smkuksool[.]com
2a01:4f9:3081:3098:0:0:0:2
services.ssh.server_host_key.fingerprint_sha256: 92709a98601c28a87fa307e63ae8bc60f870c6b9533a2d50bdb2c16fda205c37
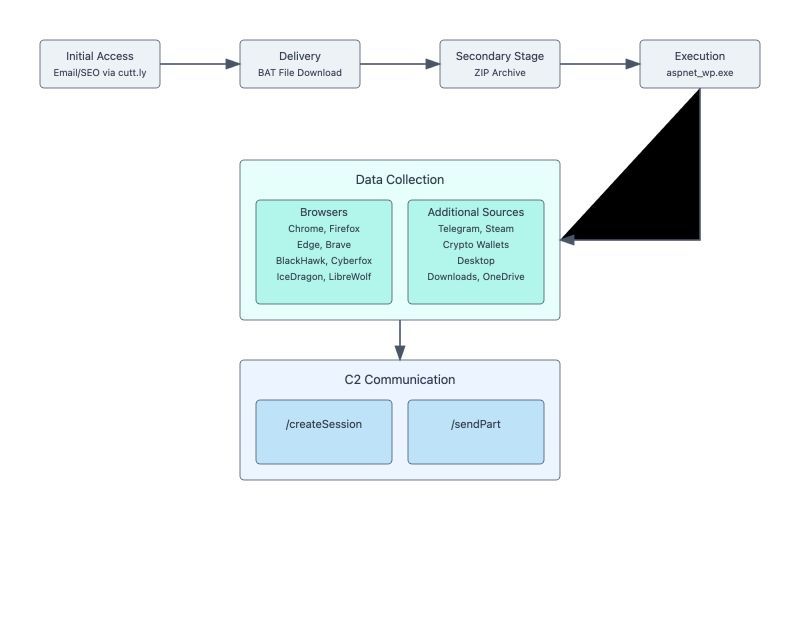
1) 45.89.196[.]115 - C2 and stealer panel
2) 104.22.0[.]232 - cutt[.]ly (Cloudflare)
1) hxxps://cutt[.]ly/guessintegrates - (initial URL)
2) hxxps://kyfjlijv[.]ru/guessintegrates.bat (Initial stage BAT file generated with Kodiac and zip file)
3) hxxp://45.89.196[.]115/core/createSession - C2
1) 45.89.196[.]115 - C2 and stealer panel
2) 104.22.0[.]232 - cutt[.]ly (Cloudflare)
1) hxxps://cutt[.]ly/guessintegrates - (initial URL)
2) hxxps://kyfjlijv[.]ru/guessintegrates.bat (Initial stage BAT file generated with Kodiac and zip file)
3) hxxp://45.89.196[.]115/core/createSession - C2
- Update systems to version 10.2.1.14-75sv or higher
- Review and implement geographic access controls
- Enable multi-factor authentication for all users
- Scan appliance for unauthorized web shells
- Check for connections originating from the appliance
- Update systems to version 10.2.1.14-75sv or higher
- Review and implement geographic access controls
- Enable multi-factor authentication for all users
- Scan appliance for unauthorized web shells
- Check for connections originating from the appliance
- United States
- The Netherlands
- Russia
ASN providers:
- 3xK Tech GmbH
- Namecheap, Inc.
- Comcast Cable Communications, LLC
- Additional regional ISPs
- United States
- The Netherlands
- Russia
ASN providers:
- 3xK Tech GmbH
- Namecheap, Inc.
- Comcast Cable Communications, LLC
- Additional regional ISPs