In this week's @thorcollective.bsky.social post, Sai Molige introduces the LAYER approach, turning strategy into practical threat hunting moves.
dispatch.thorcollective.com/p/the-power-...
#infosec #threathunting #thrunting #blueteam #threatdetection #THORcollective

#infosec #threathunting #thrunting #blueteam #threatdetection #THORcollective
Every payload has a soul - and understanding it makes us better hunters.
medium.com/@cyb3r-hawk/...

Every payload has a soul - and understanding it makes us better hunters.
medium.com/@cyb3r-hawk/...
mshta.exe → Scheduled Tasks → IEX execution.
#ThreatHunting #DetectionEngineering #MalwareAnalysis #DefenseEvasion
mshta.exe → Scheduled Tasks → IEX execution.
#ThreatHunting #DetectionEngineering #MalwareAnalysis #DefenseEvasion
medium.com/@cyb3r-hawk/...
medium.com/@cyb3r-hawk/...
#cybersecurity #threathunting #thrunting #THORcollective
#cybersecurity #threathunting #thrunting #THORcollective
#infosec #threathunting #thrunting #blueteam #threatdetection #THORcollective
In this week's @thorcollective.bsky.social post, Sai Molige introduces the LAYER approach, turning strategy into practical threat hunting moves.
dispatch.thorcollective.com/p/the-power-...
#infosec #threathunting #thrunting #blueteam #threatdetection #THORcollective

#infosec #threathunting #thrunting #blueteam #threatdetection #THORcollective
Read it at lnkd.in/g5fefgbq
Read it at lnkd.in/g5fefgbq
Check it out:
youtu.be/ndOpYFiabbc?...
Check it out:
youtu.be/ndOpYFiabbc?...
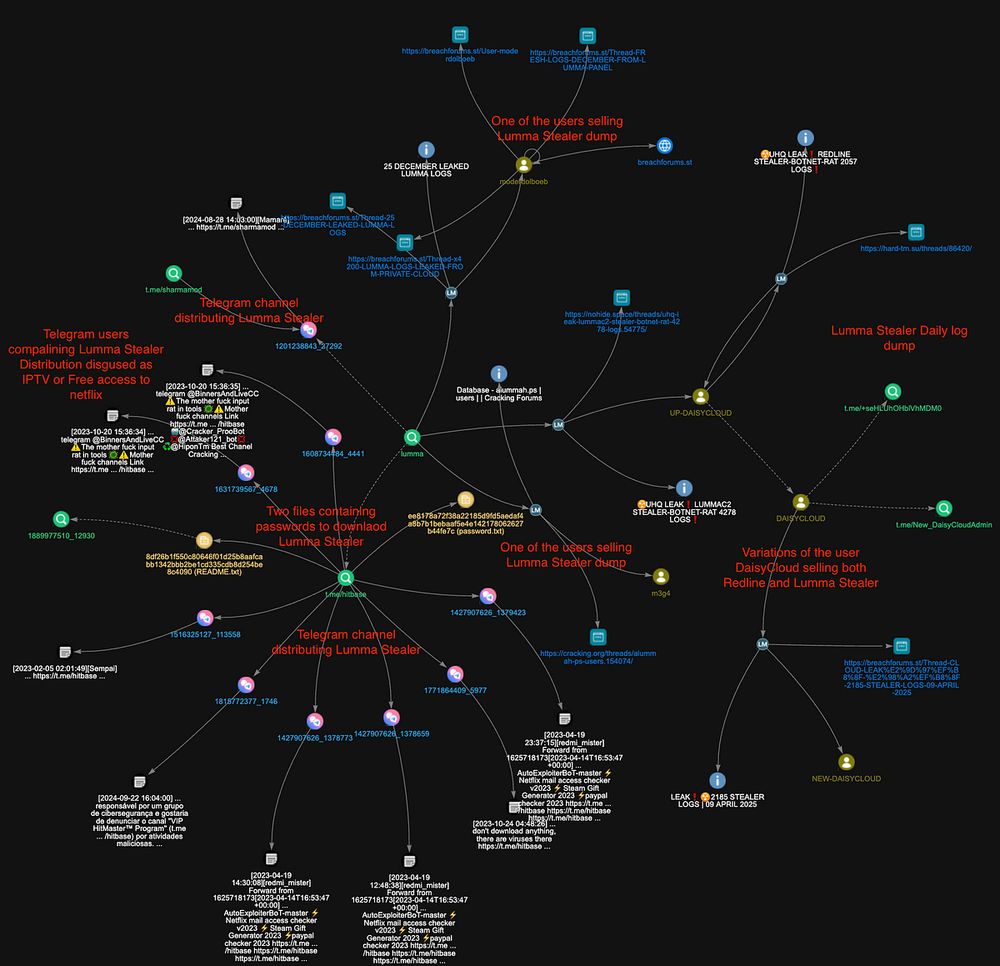
Following the trend of infostealers, while a recent campaign of AMOS stealer targeted macOS users (lnkd.in/gD8Da4mv), a new Windows-focused stealer called Amatera was observed during my recent intrusion analysis.
#Amatera #infoStealer #windows #telegram #crypto #cyber #security
Following the trend of infostealers, while a recent campaign of AMOS stealer targeted macOS users (lnkd.in/gD8Da4mv), a new Windows-focused stealer called Amatera was observed during my recent intrusion analysis.
#Amatera #infoStealer #windows #telegram #crypto #cyber #security
#macos #Atomic #infostealer #MachO #brew #SEO #google #ads #telegram #google #Chromium #crypto #wallet #cyber #security #site #impersonation
#ThreatHunting #Research #Cybersecurity
medium.com/p/90e020ffcf...
#ThreatHunting #Research #Cybersecurity
medium.com/p/90e020ffcf...
lnkd.in/g55hiBcP
#ICS #engineering #workstations #Discord
lnkd.in/g55hiBcP
#ICS #engineering #workstations #Discord
#threathunting
#threathunting
open.substack.com/pub/cyb3rsec...
#ThreatHunting #Detection #Engineering #User #agent #analysis
open.substack.com/pub/cyb3rsec...
#ThreatHunting #Detection #Engineering #User #agent #analysis
#CVE #SonicWall #SMA100 #ThreatIntel #SSL #VPN #vulnerabilities
#CVE #SonicWall #SMA100 #ThreatIntel #SSL #VPN #vulnerabilities
It discusses threat-hunting in Microsoft Teams for social engineering techniques used by BlackBasta actors. Will go over hunting queries using Microsoft 365 logs to detect anomalous patterns.
www.linkedin.com/pulse/threat...

It discusses threat-hunting in Microsoft Teams for social engineering techniques used by BlackBasta actors. Will go over hunting queries using Microsoft 365 logs to detect anomalous patterns.
www.linkedin.com/pulse/threat...

