https://intellisec.de/chris
www.bifold.berlin/news-events/...
@chwress.bsky.social @tuberlin.bsky.social @kit.edu

www.bifold.berlin/news-events/...
@chwress.bsky.social @tuberlin.bsky.social @kit.edu
Everybody is welcome and stay around for the Q&A afterwards.

🌐 https://eurosp2026.ieee-security.org/cfw.html
⏱️ Deadline: Oct 2̶4̶t̶h̶ 30th AoE
📍Lisbon, PT

🌐 https://eurosp2026.ieee-security.org/cfw.html
⏱️ Deadline: Oct 2̶4̶t̶h̶ 30th AoE
📍Lisbon, PT
@chwress.bsky.social, @kumarde.bsky.social, @aurore-fass.bsky.social

@chwress.bsky.social, @kumarde.bsky.social, @aurore-fass.bsky.social
EuroS&P is the premier, European forum for security & privacy research. The main conference is accompanied by a series of workshops. Be part of it! 😎
🌐 https://eurosp2026.ieee-security.org/cfw.html
⏱️ Deadline: Oct 24th AoE
📍Lisbon, PT

EuroS&P is the premier, European forum for security & privacy research. The main conference is accompanied by a series of workshops. Be part of it! 😎
🌐 https://eurosp2026.ieee-security.org/cfw.html
⏱️ Deadline: Oct 24th AoE
📍Lisbon, PT
🏆 Distinguished Artifact Awards
🏆 Distinguished Reviewer Awards
⭐ Noteworthy Reviewer Recognition
🥷 Ninja Reviewer Recognition
secartifacts.github.io/usenixsec202...
And thank you all for your help!
CC @pvadrevu.bsky.social Tiago Heinrich




🏆 Distinguished Artifact Awards
🏆 Distinguished Reviewer Awards
⭐ Noteworthy Reviewer Recognition
🥷 Ninja Reviewer Recognition
secartifacts.github.io/usenixsec202...
And thank you all for your help!
CC @pvadrevu.bsky.social Tiago Heinrich
🌐 https://intellisec.de/research/adv-code
(1/3)



🌐 https://intellisec.de/research/adv-code
(1/3)

Details: is.mpg.de/events/speci...
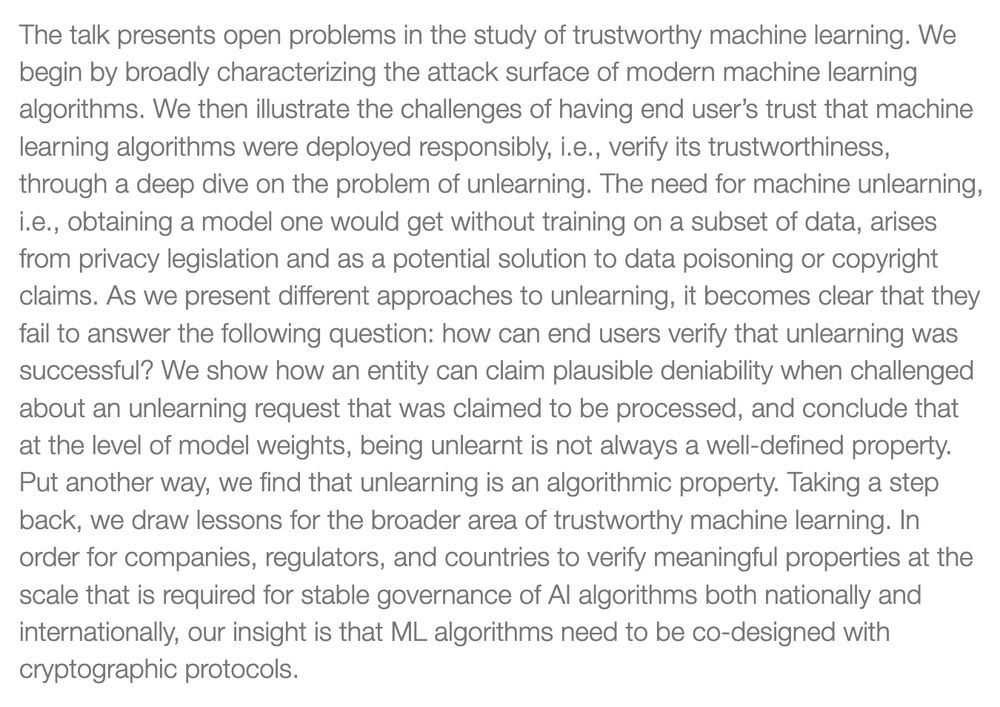
Details: is.mpg.de/events/speci...
Everybody is welcome. See you there! 🤗
Everybody is welcome. See you there! 🤗
🗞️ intellisec.de/pubs/2025-nd...
Congrats Liam and Julian 💪🥟, and thank you @gannimo.bsky.social and @tregua.bsky.social for the collaboration!
🗞️ intellisec.de/pubs/2025-nd...
Congrats Liam and Julian 💪🥟, and thank you @gannimo.bsky.social and @tregua.bsky.social for the collaboration!
🗞️ https://intellisec.de/pubs/2025-aaai.pdf
💻️ https://intellisec.de/research/harvey

🗞️ https://intellisec.de/pubs/2025-aaai.pdf
💻️ https://intellisec.de/research/harvey
PDFs support Javascript, so Emscripten is used to compile the TinyEMU emulator to asm.js, which runs in the PDF. It boots in about 30 seconds and emulates a riscv32 buildroot system.
linux.doompdf.dev/linux.pdf
github.com/ading2210/li...
PDFs support Javascript, so Emscripten is used to compile the TinyEMU emulator to asm.js, which runs in the PDF. It boots in about 30 seconds and emulates a riscv32 buildroot system.
linux.doompdf.dev/linux.pdf
github.com/ading2210/li...
Today, Julian presents our work on implanting machine learning backdoors in hardware at @acsacconf.bsky.social. Our backdoors reside within a hardware ML accelerator, manipulating models on-the-fly and invisible from outside.
mlsec.org/docs/2024-ac...
1/3

Today, Julian presents our work on implanting machine learning backdoors in hardware at @acsacconf.bsky.social. Our backdoors reside within a hardware ML accelerator, manipulating models on-the-fly and invisible from outside.
mlsec.org/docs/2024-ac...
1/3
💻️ xaisec.org/makrut
🗞️ intellisec.de/pubs/2024-ac...

💻️ xaisec.org/makrut
🗞️ intellisec.de/pubs/2024-ac...
#ML #AI #cybersecurity

#ML #AI #cybersecurity